15.4.1 Authenticated encryption with associated data
In this section, by associated data we mean any data that should be authenticated but not encrypted. There are some scenarios where it is useful to have such data.
For example, say you want to transmit a network packet composed of a header and a payload. You can encrypt the payload to prevent anyone but the legitimate receiver (or a group of legitimate receivers if you use a group key) from accessing it, but you can’t encrypt the header as it contains information needed to route the packet to the correct recipient. At the same time, you still want to authenticate the header so that the receiving party can verify the packet’s authenticity, that is, verify that it actually comes from the expected sender.
In such a situation, you can use an AEAD algorithm. In an AEAD algorithm, cleartext data (the associated data) is attached to a ciphertext along with an authentication tag T. If the cleartext or the ciphertext is corrupted, the authentication tag cannot be validated by the receiver and the ciphertext will not be decrypted.
Formally, we can define the AEAD operation as:
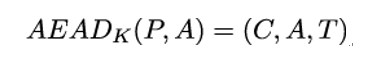
where K is the secret key, P is the plaintext, and A is the associated data. The output of the AEAD operation is a triple consisting of the ciphertext C, the associated data A (which is unencrypted), and an authentication tag T. As required, AEAD leaves A unchanged, while the ciphertext C is the encryption of the plaintext P. The authentication tag T depends on both C and A. Therefore, the receiver can only successfully verify T if both C and A have not been modified.
Conversely, we can define authenticated decryption with associated data (ADAD) as:
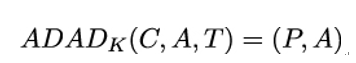
If we perform AEAD with empty authenticated data A, it becomes a normal authenticated cipher AE. If we instead leave the plaintext P empty, AEAD becomes a MAC.
Because an AEAD cipher provides confidentiality as well as message integrity and authentication, it eliminates the need to implement a separate MAC algorithm like HMAC. Among other things, this allows you to reduce the number of algorithms a TLS endpoint must implement.