14.5 Block ciphers in TLS 1.3
In TLS, block ciphers are used for protecting the confidentiality and integrity of data transmitted over the TLS Record layer. More precisely, a block cipher is used for encrypting TLSInnerPlaintext, the plaintext transmitted by Alice and Bob, into encrypted˙record in TLSCiphertext structure that is, in turn, transmitted over the wire:
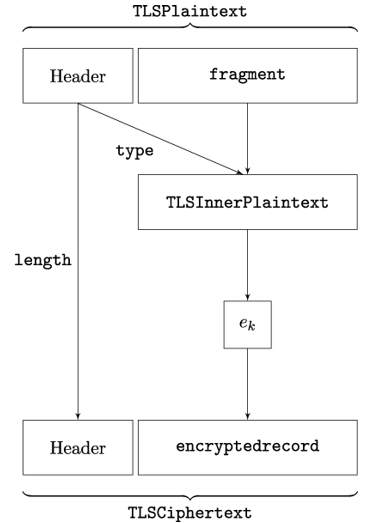
Figure 14.15: Encryption at the TLS Record layer
The encryption process is illustrated in Figure 14.15. The fragment field in the TLSPlaintext structure contains the actual payload data. The type field in TLSPlaintext contains the subprotocol type, that is, a numeric value encoding the TLS subprotocol type this data has. The enumeration of valid TLS subprotocol types is shown in Listing 14.1.
The subprotocol type and the actual payload are combined into the TLSInnerPlaintext data structure shown in Listing 14.1. This data is then encrypted using a block cipher into the encrypted˙record field in TLSCiphertext:
Note that the content type of TLSCiphertext, that is, the opaque˙type field, is always set to 23, the numeric code for application˙data. This is done in order to hide the actual content type from Eve. The actual type of the TLS record as well as its length – stored in the zeros field of TLSInnerPlaintext – is transmitted within the encrypted field encrypted˙record.
Listing 14.1: TLS 1.3 data structures used in its protocol layer
enum {
invalid(0),
change_cipher_spec(20),
alert(21),
handshake(22),
application_data(23),
(255)
} ContentType;
struct {
ContentType type;
ProtocolVersion legacy_record_version;
uint16 length;
opaque fragment[TLSPlaintext.length];
} TLSPlaintext;
struct {
opaque content[TLSPlaintext.length];
ContentType type;
uint8 zeros[length_of_padding];
} TLSInnerPlaintext;
struct {
ContentType opaque_type = application_data; /* 23 */
ProtocolVersion legacy_record_version = 0x0303; /* TLS v1.2 */
uint16 length;
opaque encrypted_record[TLSCiphertext.length];
} TLSCiphertext;
14.6 Summary
In this chapter, we learned what block ciphers are (encryption functions mapping plaintext blocks of fixed size b onto ciphertext blocks of the same size b), what design principles are used to construct block ciphers (confusion and diffusion), and what theoretical constructions are used to model block ciphers (pseudorandom permutations).
Moreover, we covered iterated block ciphers and substitution-permutation networks, the two major paradigms for designing secure block ciphers. We then studied in detail how AES, the block cipher chosen as a result of a world-wide call for algorithms by the US standardization body NIST, works. Finally, we highlighted the most common modes of operation of block ciphers, including their working principle, advantages, and disadvantages.
In the next chapter, we will take a detailed look at one more mode of operation. It is called Authenticated Encryption with Additional Data (AEAD) and plays a crucial role in TLS 1.3. In contrast to the other modes of operation discussed in this chapter, AEAD combines encryption and message authentication in a single algorithm. As a result, in TLS 1.3, AEAD is used to turn plaintexts into encrypted and authenticated cipher texts, which are then transmitted over the wire by Alice and Bob.